Microsoft AZ-900 Exam Notes
Table of Contents
- 1. Microsoft Azure Fundamentals: Describe cloud concepts
- 2. Microsoft Azure Fundamentals: Describe Azure Architecture and Services
- 2.1. What is Microsoft Azure
- 2.2. Get Started with Azure Accounts
- 2.3. Describe Azure Physical Infrastructure:
- 2.4. Describe Azure management infrastructure
- 2.5. Describe Azure Compute and Networking Services
- 2.5.1. Describe Azure Virtual Machines:
- 2.5.2. Describe Azure Virtual Desktop:
- 2.5.3. Describe Azure Containers:
- 2.5.4. Describe Azure Functions:
- 2.5.5. Describe Application Hosting Options
- 2.5.6. Describe Azure Virtual Networking
- 2.5.7. Describe Azure Virtual Private Networks (VPN):
- 2.5.8. Describe Azure ExpressRoute:
- 2.5.9. Describe Azure DNS:
- 2.6. Describe Azure Storage Services
- 2.7. Describe Azure Identity, Access and Security
- 2.7.1. Describe Azure Directory Services
- 2.7.2. Describe Azure Authentication Methods
- 2.7.3. Describe Azure External Identities
- 2.7.4. Describe Azure Conditional Access
- 2.7.5. Describe Azure Role-Based Access Control (RBAC)
- 2.7.6. Describe Zero Trust Model
- 2.7.7. Describe defense-in-depth
- 2.7.8. Described Microsoft Defender for Cloud
- 3. Microsoft Azure Fundamentals: Describe Azure Management and Governance
1. Microsoft Azure Fundamentals: Describe cloud concepts
1.1. Describe Cloud Computing
1.1.1. Learning Objectives:
- Define cloud computing.
- Describe the shared responsibility model.
- Define cloud models, including public, private, and hybrid.
- Identify appropriate use cases for each cloud model.
- Describe the consumption-based model.
- Compare cloud pricing models.
1.1.2. What is Cloud Computing?
- Delivery of computing services over internet
- VMs, Storage, DBs, Networking
- Compute Power: allows for flexible amounts of compute, instead of strict 4/8/16gb or specific hardware.
- Storage: allows for flexible amounts of storage (as well as backups), instead of specific hardware requirements.
- Why?
- As business needs change, compute and storage can be as flexible as possible
1.1.3. Shared Responsibility Model
- Example Corporate Datacenter:
- Company responsible for storage, security, maintenance/replacement.
- IT department responsible for infrastructure and necessary software for upkeep
- Also responsible for patching and versioning
- With Shared Responsiblity:
- Physical security, power, cooling handled by provider.
- Data, information, network security handled by consumer.
- Cloud Service Types:
- Infrastructure as a Service (IaaS)
- Responsibility leans towards consumer
- Provider only responsible for physical aspects
- security of hardware
- power
- internet access
- Platform as a Service (PaaS)
- Median responsiblity between IaaS and SaaS
- Software as a Service (Saas)
- Responsibility leans towards provider
- Consumer only worries about data (mostly) as well as devices and accounts
- Infrastructure as a Service (IaaS)
- Responsibilities:
- Consumer (Minimum):
- Information and Data stored in the cloud
- Devices allowed to connect to cloud (phones, computers)
- Accounts and Identities of people/services/devices * Cloud Provider (Minimum):
- Physical datacenter
- Physical network
- Physical host machines
- Changes based on service model:
- Operating Systems
- Network Configuration
- Applications and Software
- Identity and Infrastructure
- Consumer (Minimum):
1.1.4. Cloud Models:
- Deployment Type of Cloud Resources
| Public Cloud | Private Cloud | Hybrid Cloud |
|---|---|---|
| No expenditures to scale up | Complete Control over resources/stability | Most Flexible (both options) |
| Quick provisioning | Complete Control over data | Pick between both options |
| Pay as you go | Own your own hardware | Both |
| Don’t have full access | Responsible for maintenance and upgrades | Security/Compliance/Legal managed manually |
- Private:
- Cloud used by single entity
- Can be hosted onsite in your own datacenter
- Subject to your own corporate network access
- Public:
- Entirely third-party provider cloud
- General Availability
- Hybrid:
- Private cloud that can request public cloud resources when necessary
- Specific services can be kept private, while others can be scaled publicly when necessary.
- Multi-Cloud:
- Multiple public cloud providers
- Manage resources and security in two public environments
- Azure Arc:
- Technologies to manage cloud environments, usable on public/private/hybrid/multi
- Azure VMWare Solution:
- Run VMWare workloads on Azure machines with seamless integration and scalability
1.1.5. Consumption-based Model
- Two types of expense:
- Capital Expense (CapEx)
- 1-time, up-front payment for tangible resources
- Operational Expenditures (OpEx)
- Leases, Subscriptions, etc.
- Capital Expense (CapEx)
1.2. Describe benefits of using cloud services
1.2.1. Benefits of High Availability and Scalability in the Cloud
1.2.2. Benefits of Reliability and Predictability in the Cloud
- Reliability
- Ability of a system to recover from failures and continue to function.
- Cloud naturally supports reliable and resilient infra
- Even when one region goes down, there are many other regions around the world that can serve business needs.
- Predictability
- Performance Predictablity
- Predicting resources needed to account for demand.
- i.e Autoscaling, Load Balancing, High Availability
- Cost Predictability
- Predicting/Forecasting cloud spending
- Track resource use in real-time, monitor efficiency of resources, use data analytics to plan future resource deployments.
- Tools for estimating cloud spend:
- Total Cost of Ownership (TCO)
- Pricing Calculator
- Performance Predictablity
1.2.3. Benefits of Security and Governance in the Cloud
- Support for governance and compliance for businesses and enterprise
- “Cloud Based Auditing”
- Set templates ensure corporate and government regulatory standards are met
- Allow for updating older resources to comply with new requirements
- Software patches and updates can also be automatically applied
- IaaS allows self-management of software and OS
- PaaS and SaaS can take care of OS, Software and maintenance.
- Cloud can mitigate DDoS attacks on your services.
1.2.4. Benefits of manageability in the Cloud
1.3. Describe Cloud Service Types
1.3.1. Describe Infrastructure as a Service (IaaS)
- Most flexible category of cloud services
- Most control of resources
- Cloud provider maintains hardware, network and physical security.
- Consumer responsible for:
- OS
- Configuration (Network, DB, Storage)
- Maintenance
- Consumer responsible for:
- “Renting hardware in a datacenter”
1.3.2. Describe Platform as a Service (PaaS)
- Middle ground between IaaS and SaaS
- Cloud provider maintains:
- Physical security
- Physical infrastructure
- Network Connection
- OS
- Middleware
- Dev Tools
- Business Intelligence Services
- Licensing and Patching
- Ideal for “dev environment without maintenance”
- Common Scenarios
- Development Framework:
- PaaS provides a framework devs can build on to develop/customize cloud-based applications
- Features like scalability, reliability, availability, multi-tenancy are available
- Analytics/Business Intelligence:
- Tools provided with PaaS allow businesses to analyze and mine their own data, allowing insights and discovery of new patterns to improve forecasting, design decisions, investment returns, etc..
- Development Framework:
1.3.3. Describe Software as a Service (SaaS)
- Complete cloud service model
- Fully built software (Email, Financial Software, Messaging, Connectivity Software)
- Least flexible, but easiest to get running and deployed, least amount of technical knowledge/expertise necessary
2. Microsoft Azure Fundamentals: Describe Azure Architecture and Services
- Describe Azure regions, region pairs, and sovereign regions.
- Describe Availability Zones.
- Describe Azure datacenters.
- Describe Azure resources and Resource Groups.
- Describe subscriptions.
- Describe management groups.
- Describe the hierarchy of resource groups, subscriptions, and management groups.
2.1. What is Microsoft Azure
- continually expanding set of cloud services
2.1.1. What does Azure Offer?
- Trusted platform
- AI/Cloud Services
- Secure
2.1.2. What Can I do with Azure?
- Run existing applications on VMs
- AI/ML Services
- Storage Solutions
2.2. Get Started with Azure Accounts
- Azure subscription required
- Once account is made, can split different use cases into different subscriptions for billing purposes:
- Separate subscriptions for dev, sales, marketing
- Each subscription holds resource groups
- Once account is made, can split different use cases into different subscriptions for billing purposes:
2.2.1. What is the Azure Free Account?
- Free access to certain services (12 months)
- Credit for first 12 months
- Free access to certain dev tools
2.2.2. What is the Microsoft Learn Sandbox?
- Temporary sub for learning
2.3. Describe Azure Physical Infrastructure:
2.3.1. Physical Infrastructure:
- Datacenters (dedicated cooling/power/infrastructure)
- Grouped into AZ (availability zones) or regions
2.3.2. Regions:
- Geographical area with at least one (but may be many) datacenters nearby and networked together.
2.3.3. Availability Zones:
- Physically separate datacenters within a region.
- 1+ datacenters with independent power, cooling, networking
- To ensure resiliency, a minimum of three separate availability zones are present in all availability zone-enabled regions.
- However, not all Azure Regions currently support availability zones.
2.4. Describe Azure management infrastructure
2.4.1. Resources / Resource Groups
- Resource is basic building block of Azure.
- Anything created, provisioned, deployed is a resource
- Resource Groups are groupings of resources.
- Created resources are required to be placed in a resource group.
- Can contain many resource in one resource group, but resources can only belong to one group
- Resource Groups cannot be nested within one another.
- Actions apply across all resources within a group, including deletion and access control.
2.4.2. Subscriptions:
- Unit of management, billing and scale.
- Allow for logical organization of billing resources.
- All Azure accounts are initialized with a subscription, which provides authenticated and authorized access to Azure products/services.
- Subscriptions allow provisioning of resources/groups
- Subscriptions link to Azure accounts, which is an entry in Entra ID (Active Directory) or in a directory that Entra ID trusts.
- Accounts:
- Accounts can have multiple subscriptions, but always has one to start with.
- Multi-subscriptions allow different billing models and access-management policies.
- Subscription Boundaries:
- Billing Boundary:
- how an account is billed for using Azure different
- subscription has a separate report and invoice
- Access Control Boundary:
- Access-management policies applied at subscription level
- Separate subscriptions can be created to reflect how your organization is structured.
- Manage and control access to resources that users provision with specific subscriptions.
- Billing Boundary:
- Create Additional Azure Subscriptions:
- Reasons:
- Environments (dev/test, security, compliance)
- Organlizational Structures (lower-cost resources per team, IT has full access)
- Billing (production vs dev vs test workload pricing)
- Reasons:
2.4.3. Azure Management Groups:
- Resource -> Resource Groups
- Resource Groups -> Subscriptions
- Subscriptions -> Management Groups
- 10,000 management groups are supported per directory
- Management group trees support 6 levels of depth (not including root or subscription)
- Each management group + subscription can only support one parent
2.4.4. Overall Hierarchy:
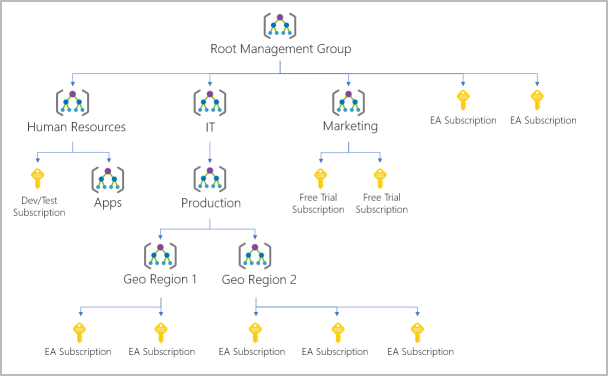
2.5. Describe Azure Compute and Networking Services
2.5.1. Describe Azure Virtual Machines:
- VMs are part of IaaS as a virtualized server
- Ideal when you need:
- Total Control over OS
- Ability to run Custom Software
- Custom Hosting Configurations
- Flexible for virtualization without maintaining physical hardware.
- Custom preset images are usable for rapid provisioning and deployment.
- Scale VMs in Azure
- Single VMs for testing / dev / minor tasks
- Groupings can be managed using Scale Sets and Availability Sets.
- Scale Sets
- Group of Identical, Load-Balanced VMs
- Central Management, Configuration and Updates
- Instances can increase/decrease based on demand, or on a scheduled basis.
- Automatically deploys a load balancer to ensure efficient use.
- Useful for compute, big data, container workloads.
- Availability Sets
- Designed to ensure maximum availability, including staggered updates and varied power/network connectivity
- When to Use VMs
- Testing/Deployment (easy provisioning and deletion)
- General Running Applications (no need for hardware)
- Extending datacenter to cloud (SharePoint and other local MS services can run on Azure)
- Disaster Recovery (Create VMs to backup primary data center)
- VM Resources
- Size (processor cores / RAM)
- Storage Disks (HDD, SSD, etc.)
- Networking (Virtual Network, Public IP, Port Configuration)
2.5.2. Describe Azure Virtual Desktop:
- Cloud-Hosted Windows from any location.
- Centralized Security Management via Entra ID or RBAC (Role-Based Access Control)
- Data/Apps separate from hardware, no risk of confidential data left on personal devices.
- Isolation between single and multi-session environments
2.5.3. Describe Azure Containers:
- Virtualization Environment
- Multiple Containers per physical/virtual host
- No management of OS
- Light weight / more agile method compared to VMs
- Quick restart if crash or hardware issue.
- Azure supports Docker
- Azure Container Instances:
- Fastest/Simplest way to run container
- PaaS, upload container
- Azure Container Apps:
- PaaS, but includes load balancing and scaling
- Use Containers in Your Solutions:
- Often used with microservice architecture
- Containers allow scaling back-end separately to improve performance, without impacting front-end and storage.
2.5.4. Describe Azure Functions:
- event-driven, serverless copmute
- Benefits of Azure Functions
- Ideal when no concern for platform/infra
- Response to Event (REST / http common), timer, or message
- used for small workloads
- scale automatically based on demand, with no dedicated hardware
- charged only for CPU time used while your function runs, and no other cost.
- When functions are Stateless, they behave as if they restart every time an event is triggered
- Stateful Functions (aka Durable Functions) have a context passed through to track prior triggers.
2.5.5. Describe Application Hosting Options
- Azure App Service:
- App Service enables build/host of web apps, background jobs, mobile back-ends, and RESTful APIs
- With NO infra cost
- Features automatic scaling and high availability, with Windows and Linux.
- Links Azure DevOps, GitHub, and other git repos for continuous deployment.
- HTTP-based
- other Features:
- Integrated Deployment/Management
- Secure Endpoints
- Quick Scaling
- Built-In Load-Balancing and Traffic Management
- Web Apps:
- ASP.net / Core
- Java
- Ruby
- Node.js
- PHP
- Pyton
- API Apps:
- Swagger Support
- Package/Publish API in Azure Marketplace
- Consumed via HTTP/HTTPS
- WebJobs:
- Run Program/Script in same context as Web App, API, Mobile
- Schedule or Triggered
- Common for background tasks
- Mobile Apps:
- Quick back-end
- Database
- Authentication with MSA, Google, X, Facebook
- Push Notifications
- Custom Logic in C# / Node.js
- SDK support for native iOS and Android, Xamarin, and React Native.
- App Service enables build/host of web apps, background jobs, mobile back-ends, and RESTful APIs
2.5.6. Describe Azure Virtual Networking
- networks and subnets enable azure services to communicate with each other
- Key networking capabilities:
- Isolation and segmentation
- Internet communication
- Communication between Azure resources
- Communication with on-premises resources
- Routing network traffic
- Filtering network traffic
- Connecting virtual networks
- Isolation and Segmentation:
- Create multiple isolated virtual networks
- Each has private IP address space (defined by public/private IP ranges)
- IP range only exists within the virtual network
- Able to be further divided into subnets
- Azure DNS available, or use internal/external DNS server
- Create multiple isolated virtual networks
- Internet Communications:
- Enable communications via public IP or load balancer
- Communicate between Azure Resources:
- Virtual networks can connect many different kinds of Azure Resources:
- App Service Environment (Power Apps)
- Azure Kubernetes Service
- VM Scale Sets
- Service Endpoints can connect to other resource types:
- Azure SQL DB
- Azure Storage Accounts
- Useful for security purposes
- Virtual networks can connect many different kinds of Azure Resources:
- Communicate with On-Premises Resources:
- Point-to-site VPN connections:
- From computer outside network into your corporate network
- Client -> Azure Virtual Network
- Site-To-Site VPN:
- On-Premises gateway to Azure VPN gateway
- Encrypted over internet
- Azure ExpressRoute:
- Dedicated private connection to Azure without internet
- Max bandwidth and security
- Point-to-site VPN connections:
- Route Network Traffic:
- Azure routes between subnets and VPNs
- Route Tables define rules on how packets should be routed
- Border Gateway Protocol
- Filter Network Traffic:
- Network Security Groups are resources that contain inbound/outbound security rules
- Can allow/deny traffic based on source/destination address, port and protocol.
- Network Virtual Appliances are specialized VMs
- Run Firewalls or Wide Area Network (WAN) optimization
- Network Security Groups are resources that contain inbound/outbound security rules
- Connect Virtual Networks:
- Virtual Network Peering: 2 Virtual Networks connect directly to each other
- Travels on Microsoft network, not public internet
- Resources in each Virtual Network to communicate with each other
- Even if in separate region
- Creates a global interconnected network through Azure.
- User-defined Routes allow control of routing tables between subnets within a Virtual Network (or peered Network)
- Virtual Network Peering: 2 Virtual Networks connect directly to each other
2.5.7. Describe Azure Virtual Private Networks (VPN):
- A VPN uses an encrypted tunnel within another network.
- Typically deployed to connect trusted private networks over an untrusted network (internet)
- Traffic is encrypted to prevent eavesdropping or MITM attacks
- VPN Gateways:
- Connect on-prem to Virtual Networks through site-to-site connections
- Connect individual devices to Virtual Networks through point-to-site connections.
- Connect Virtual Networks to other Virtual Networks through network-to-network connections.
- Policy-Based Gateway:
- Specify Static IP address of packets to be encrypted
- Evaluates each data packet against IP address sets
- Route-Based Gateway:
- IP Routing (static/dynamic) decides which inet interface to use when sending a packet.
- More resilient than Policy-based.
- Use-Cases:
- Connections between Virtual Networks
- Point-to-Site connections.
- Multisite connections.
- Use of Azure ExpressRoute gateway.
- High-Availability Scenarios:
- VPN should be highly available and fault tolerant
- Active/Standby (Default):
- 2 instances (even if you only see one)
- When maintenace affects service, the other swaps in within a few seconds
- When disruptions occur, up to 90 second failover time.
- Active/Active:
- BGP Routing allows 2 unique instances up at all time with no failover time
- ExpressRoute Failover:
- ExpressRoute circuits are resilient, but not against physical issues
- VPN Gateway for alternate connection to Virtual Networks.
- Zone-Redundant Gateways:
- Works across AZs and require different gateway SKUs and Standard public IP Addresses
2.5.8. Describe Azure ExpressRoute:
- Extend on-prem into Microsoft cloud using an ExpressRoute Circuit
- Any-To-Any (IP VPN)
- Point-To-Point (Ethernet)
- Virtual Cross-Connection (External Facility)
- Connections go to Microsoft cloud, not public internet.
- More Reliable
- Faster Speed
- Better Latency
- Higher Security
- Features / Benefits:
- Connectivity to Microsoft Cloud Services:
- Office 365
- Dynamics 365
- Azure Compute
- Azure Cloud
- Global Connectivity:
- Exchange Data across on-prem sites on different continents using ExpressRoute circuits instead of public internet.
- Dynamic Routing:
- BGP protocol
- Built-In Redundancy:
- ExpressRoute Circuits have redundancy options for your corporate network.
- Connectivity to Microsoft Cloud Services:
- Connectivity Models:
- CloudExchange Colocation:
- Facilities colocated at a cloud exchange (i.e at an ISP)
- Can request a virtual cross-connect to Microsoft Cloud
- Point-to-Point Ethernet:
- Self-Explanatory
- Any-To-Any Networks:
- Provide connections to offices and datacentres
- Works like the connection between your datacentre and branch offices.
- Direct from ExpressRoute sites:
- Connect direct in a specific location
- Dual 100 Gbps or 10-Gbps
- CloudExchange Colocation:
- Security Considerations:
- No public internet use
- Private connection from you to Microsoft Cloud
- DNS Queries, Certificate checking, Azure CDN are on public internet.
2.5.9. Describe Azure DNS:
- Hosting for DNS domains using Azure infrastructure.
- Manage DNS records and domains using the same tools as your other services.
- Cannot use Azure DNS to buy a domain, but can use App Service or a third-party.
- Benefits:
- Reliability and Performance:
- Global Network
- AnyCast Networking (closest server answers query)
- Fast performance
- High Availability
- Security:
- Azure RBAC
- Activity Logs
- Resource Locking
- Ease of Use:
- DNS for Azure and external services
- Part of Azure portal
- Available with Azure CLI
- Configurable with REST API and SDKs
- Customizable Virtual Networks with Private Domains:
- Private Custom DNS names instead of Azure names
- Alias Records:
- Azure DNS supports Alias Record Sets
- Refer to an Azure Resource (Public IP, Traffic Manager Profile, CDN Endpoint)
- Alias record auto updates for dynamic IP Addresses
- Azure DNS supports Alias Record Sets
- Reliability and Performance:
2.6. Describe Azure Storage Services
2.6.1. Describe Azure storage accounts:
- Unique Namespace for Data over HTTP/S
- Storage Options:
- Locally Redundant Storage (LRS)
- Geo Redundant Storage (GRS)
- Read-Access Geo Redundant Storage (RA-GRS)
- Zone Redundant Storage (ZRS)
- Geo Zone Redundant Storage (GZRS)
- Read-Access Geo Zone Redundant Storage (RA-GZRS)
| Type | Supported Services | Redundancy | Usage |
|---|---|---|---|
| Standard general-purpose v2 | Blob Storage, Data Lake, Queue, Table, Azure Files | All Options | Standard Storage Type for most scenarios |
| Premium Block Blobs | Blob Storage, Data Lake | LRS, ZRS | Premium for block/append blobs for high transaction rates or smaller objects or low-latency |
| Premium File Shares | Azure Files | LRS, ZRS | File Shares Only, Enterprise-scale. Supports Server Message Block (SMB) and NFS |
| Premium Page Blobs | Page Blobs Only | LRS | Premium for page blobs only |
2.6.2. Describe Azure Storage Redundancy:
- Redundancy in Primary Region:
- Always replicated 3x
- Replication Option is either LRS or ZRS
- Locally Redundant Storage (LRS):
- Replicates within a single data center in primary region
- 11 9s of durability 99.999999999%
- Lowest cost Redundancy
- Protects against hardware failures
- Does not protect against data center destruction or damage
- Zone-Redundant Storage (ZRS):
- ZRS replicates across 3 AZs in the primary region
- 12 9s of durability
- Works even when a zone is unavailable
- No remounting of files from clients
- Azure will repoint DNS to proper data centre
- Ideal for High Availability or restricting replication in a certain region
- Redundancy in a Secondary Region:
- Paired Secondary Region is generated by Azure Region Pairs, and cannot be changed.
- Data in secondary region is not available for read/write unless failover or primary region is unavailable
- Data is replicated to secondary region asynchronously, which means data can still be lost if something happens in that time
- Usually less than 15 minute Recovery Point Objective (RPO), but not defined in the Service Level Agreement (SLA)
- Geo-Redundant Storage (GRS):
- Uses LRS in primary region, then LRS in secondary region
- 16 9s of durability
- Geo-Zone-Redundant Storage (GZRS):
- ZRS in primary region with LRS for secondary region
- 16 9s of durability
- Recommended for maximum consistency, durabiilty, availability, performance, and resilience.
- Read Access to Data (GRS/GZRS):
- You can enable read access to secondary storage using RA-GRS and RA-GZRS
- Else it is unavailable until Failover occurs
2.6.3. Describe Azure Storage Services:
- Azure Blobs
- Massively scalable object store for text and binary
- Supports Big Data Analytics via Data Lake
- Azure Files
- Managed File Shares for cloud/on-prem
- Azure Queues
- Messaging store for application components
- Azure Disks
- Block-level storage volumes for VMs
- Azure Tables
- NoSQL option
- Benefits:
- Durable and Highly Available
- Secure
- Scalable
- Managed
- Accessible
- Azure Blobs:
- Unstructured
- Scalable with thousands of simultaneous uploads
- Not limited to common formats
- No disk management necessary
- Use Case:
- Serving Images/Documents to browser
- Storing Files
- Streaming video/audio
- Storing data for backup
- Storing data for analysis
- Access:
- HTTP/S Direct URL
- Azure Storage REST API
- Azure PWSH
- Azure CLI
- Azure Storage SDK
- Storage Tiers:
- Hot/cool/cold set at account level, or blob level
- Archive stores offline, cool/cold are still online but lower availability
- Hot access: frequent access
- Cool access: Infrequently access and stored for ~30 days
- Cold access: Infrequently access and stored for ~90 days
- Archive access: Rarely accessed and stored for ~180 days
- Azure Files:
- Fully Managed file share via Server Message Block (SMB) or Network File System (NFS)
- can be mounted concurrently by cloud or on-prem
- SMB Accessible from windows/linux/macos
- Cachable on windows servers with Azure File Sync
- NFS accessible from linux/macos
- Azure Queues:
- Store and Retrieve Messages via http/s
- Messages up to 64kb in size
- Can be combined with Azure Functions to trigger actions on message receieved.
- Azure Disks:
- Block level volumes meant for Azure VMs
- Managed, user only provisions with a VM
- Azure Tables:
- Large amounts of structured data
- NoSQL datastore with authentication in/outside of Azure
- ideal for structured, non-relational data.
2.6.4. Identify Azure Data Migration Options
- Azure Migrate:
- Unified Migration Platform (single portal)
- Integration with other tools
- Easily Access and Migrate
- Integrated Tools:
- “Discovery and Assessment”
- Assess VMWare, Hyper-V, and physical servers
- “Server Migration”
- Migrate VMWare, Hyper-V, physical servers, virtualized servers, and public cloud VMs
- “Data Migration Assistant”
- Assess SQL Servers
- Unsupported features
- New Features
- Migration Issue Identification
- Assess SQL Servers
- “App Service Migration Assistant”
- .NET and PHP web app migration
- “Data Box”
- migration of offline data to azure
- “Discovery and Assessment”
- Azure Data Box:
- Secure Data transfer over a proprietary “Data Box” storge device
- Maximum capacity of 80 TB
- Transported to and from your datacenter via mail
- Physical migration Service
- NIST 800-88r1 standards
- Disks are erased once Azure datacenter receives package.
- Secure Data transfer over a proprietary “Data Box” storge device
- Use Cases:
- Data Box is meant for 40TB or larger scenarios with no -> limited network connectivity.
- One-time migration
- Media library migration (offline tapes -> online media)
- Migrating VM farm, SQL Server, and other applications
- Moving historical data for analysis and reporting with HDInsight
- Initial bulk transfer -> Incremental transfers
- Periodic uploads
2.6.5. Identify Azure File Movement Options:
- Individual Files / Small File Groups
- AzCopy
- CLI for copying blobs/files to/from storage accounts
- upload/download/copy/sync
- Works with other cloud providers
- Only works in 1-direction
- Azure Storage Explorer
- GUI for managing files and blobs
- Windows/MacOS/Linux
- Uses AzCopy under the hood
- Azure File Sync
- Centralize file shares and compatible with Windows File Server
- Similar to CDN
- Bi-Directional Sync
- Works with SMB, NFS, FTPS
- Have as many caches as necessary
- Replace failed server with an Azure File Sync
- Use Cloud Tiering technology for replication
2.7. Describe Azure Identity, Access and Security
2.7.1. Describe Azure Directory Services
- Similar to Active Directory, hosted by Microsoft.
- AD but with high availability because Microsoft hosts it
- Who Uses Entra ID?
- IT Administrators (RBAC)
- App Developers (SSO)
- Users
- Online Service Subscribers (O365)
- What Does Entra ID do?
- Authentication
- Self-Service Password Management
- MultiFactor Authentication (MFA)
- Custom Banned Passwords
- Smart Lockout Services
- Single-Sign-On (SSO)
- Application Management
- Device Management
- Register personal devices
- Device-based conditional access
- Authentication
- Can I Connect On-Prem AD with Entra ID?
- Microsoft Entra Connect synchronizes identities between AD and Entra ID
- SSO, MFA available under both AD and Entra ID
- What is Entra Domain Services?
- Provides services for domains:
- Lightweight Directory Access Protocol (LDAP)
- Kerberos and NTLM Authentication
- Don’t need to host your own Domain Controllers (DCs)
- Can run legacy applications that can’t use modern authentication methods
- Or for cases where hitting the on-prem AD server are unnecessary
- Provides services for domains:
- How does Entra Domain Services Work?
- Define unique namespace for your domain name
- 2 Windows Server DCs are deployed in your region as a replica set
- Azure manages the DCs, including encryption and backups
- Is Information Synchronized?
- One-Way sync from Entra ID to Entra Domain Services
In hybrid on-prem, Entra Connect syncs with Entra ID which syncs to managed domain
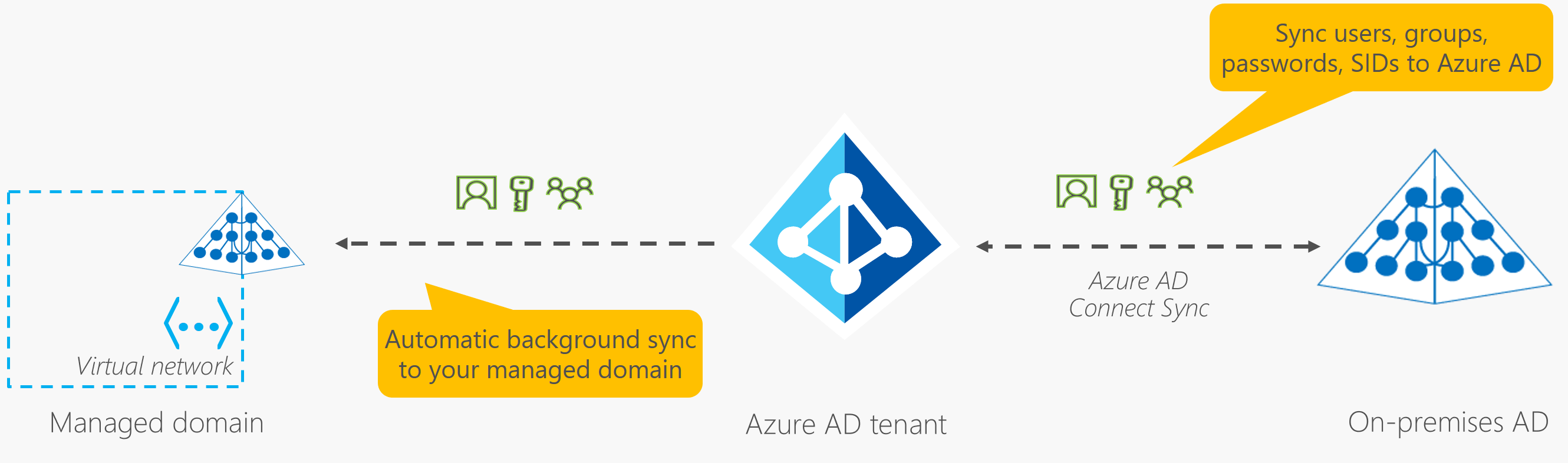
- Applications, Services and VMs in the managed domain can use Entra Domain Services mentioned above.
2.7.2. Describe Azure Authentication Methods
- Authentication:
- The process of establishing the identity of a person/service/device.
- Requires person/service/device to provide credentials to verify their identity.
- Azure supports multiple authentication methods
- Standard passwords
- Single-Sign-On (SSO)
- Multifactor Authentication (MFA)
- Passwordless
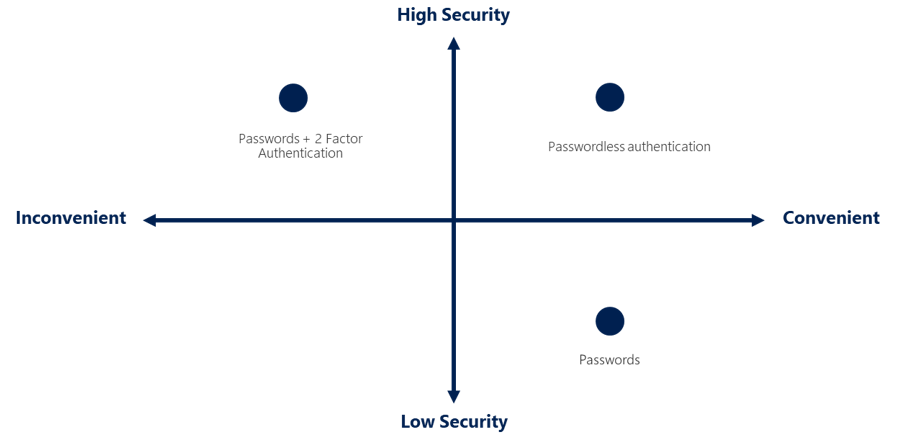
- What is Single Sign-On (SSO)?
- SSO enables users to sign in one-time and use the same credential to access multiple resources and applications from various providers.
- Initial authenticator must be trusted by providers of applications.
- Only one ID and password is required for access across applications
- As users change roles and leave organizations, access is linked to the single identity.
- SSO is only as secure as the initial authenticator (subsequent connections are based on the security of the initial authenticator)
- What is Multifactor Authentication (MFA)?
- Process of prompting for an extra form/factor of identification during the sign-in process
- MFA helps to protect against password compromise
- What is Microsoft Entra Multifactor Authentication?
- Allows additional form of auth during sign-in, such as phone call or app notification
- What is Passwordless Auth?
- Passwordless auth has to be set up on a device, and then you can be authenticated without using a password
- Microsoft global Azure and Azure Government offer 3 options:
- Windows Hello for Business
- Microsoft Authenticator App
- FIDO2 Security Keys
- Windows Hello for Business
- Ideal for workers with designated Windows PC
- Biometric/PIN credentials
- Microsoft Authenticator
- Authenticator can be used both as MFA and as just Passwordless
- Any iOS or Android phone can be used to sign up and sign in
- FIDO2 Security Keys
- Fast IDentity Online (FIDO) Alliance helps to promote open authentication standards and reduce password use.
- FIDO2 is the latest standard that incorporates the WebAuthn standard.
- Unphishable standards-based passwordless authenitcation, and is an open standard.
- Security Keys are often USB devices, but can also be Bluetooth or NFC.
- Hardware Device reduces security risks as there’s no password to guess
2.7.3. Describe Azure External Identities
- External Identity:
- A person/device/service outside your organization
- Entra External ID refers to ways you can securely interact with users outside of your organization
- Users can bring their own identities
- Corporate/Government-issued
- Social Identity (Google/Facebook)
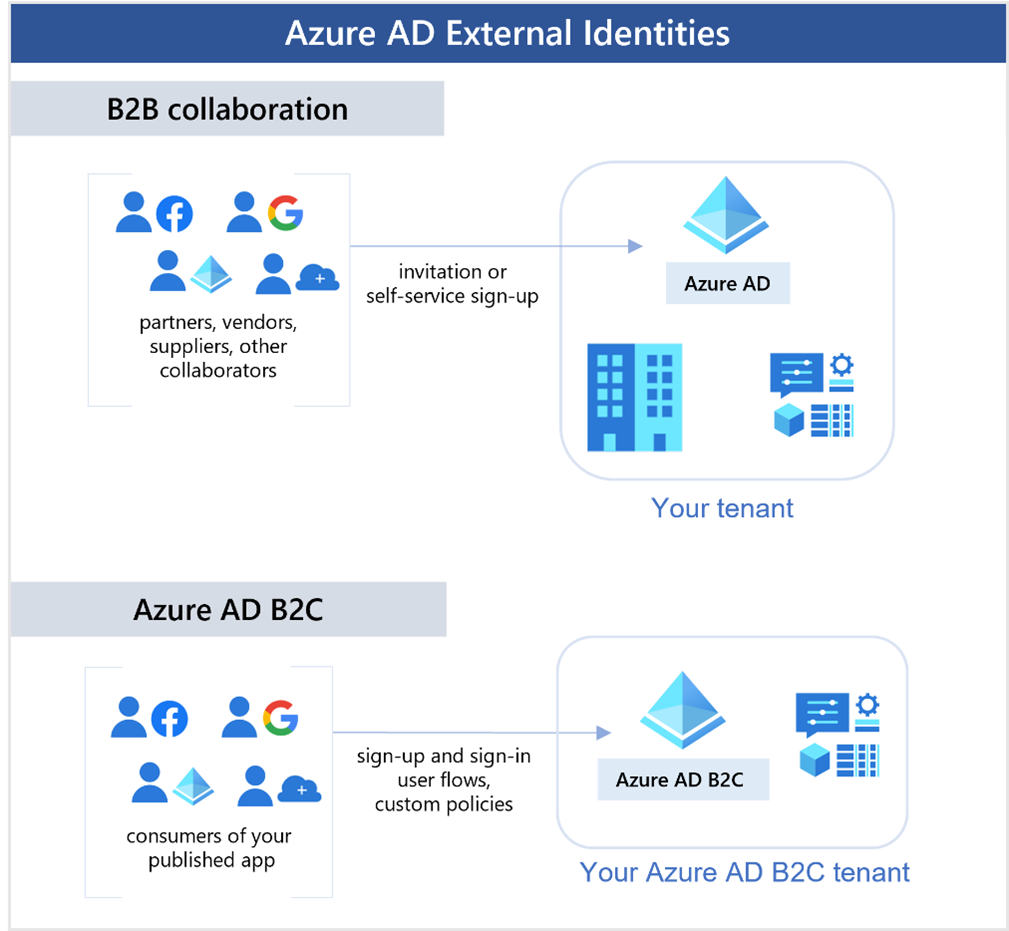
- Business to Business (B2B) Collaboration
- Use preferred identity to sign in to your applications
- Represented in your directory as guest users
- B2B Direct Connect
- Establish a mutual trust between Entra organizations for collaboration
- Supports Teams shared channels, but aren’t represented in your directory
- Active Directory Business to Consumer (B2C)
- Publish modern SaaS or custom apps (not Microsoft) to consumers/customers
- Use AD B2C to manage identity and access
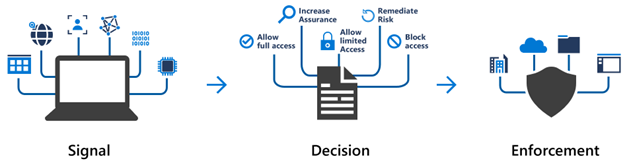
2.7.4. Describe Azure Conditional Access
- Conditional access is a tool that Entra ID uses to allow/deny access to resources based on identity signals.
- IT Administrators can:
- Empower users to be productive
- Protect organizational assets
Conditional Access allows for granular MFA experience based on known location or other signals.
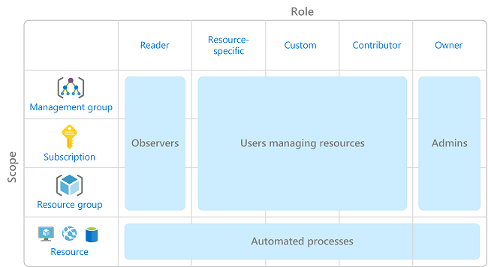
2.7.5. Describe Azure Role-Based Access Control (RBAC)
- Hierarchical access
- Parent access is inherited by children
- Management Group can manage everything under it
- Parent access is inherited by children
- Scopes:
- Management Group
- Single Subscription
- Resource Group
- Single Resource
- How is Azure RBAC Enforced?
- Any action initiated against an Azure resource through Azure Resource Manager.
- Resource Manager is a management service that provides a way to organize and secure your cloud resources
- Access through Portal, Cloud Shell, PowerShell, CLI
- Not enforced at application/data level, this should be handled by your application.
- Allow-model based
- i.e if one role gives read access and other role gives write access, you have both read & write access
- Any action initiated against an Azure resource through Azure Resource Manager.
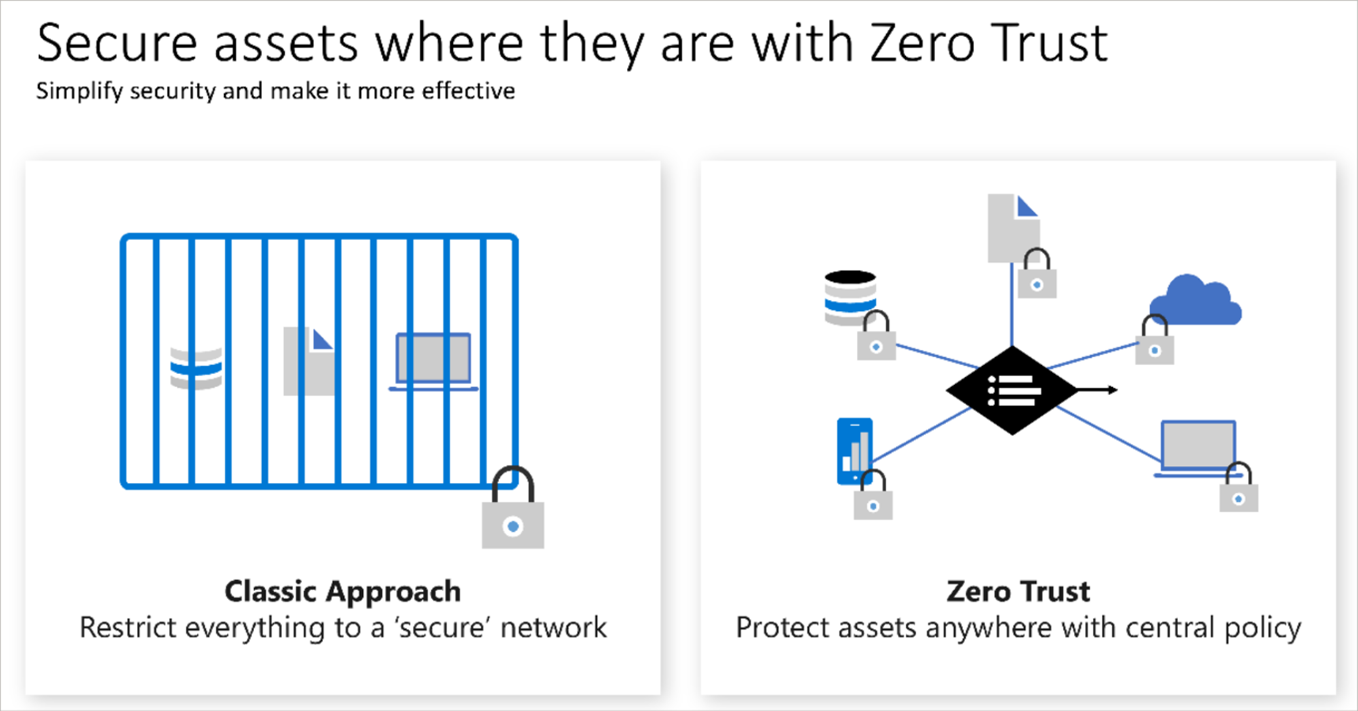
2.7.6. Describe Zero Trust Model
- Security model that assumes worst case scenario (to protect resources)
- Assumes breach at outset, and verifies requests as if they were untrusted.
- Guidelines:
- Verify Explicitly
- Always authenticate and authorize based on all available data points
- Least Privilege Access
- Limit user access with Just-In-Time (JIT) and Just-Enough-Access (JEA)
- Use risk-based adaptive policies and data protection policies.
- Assume Breach
- Minimize blast radius
- Segment access to resources
- Verify End-To-End Encryption
- Use Analytics for Visibility, Threat Detection, Defense.
- Verify Explicitly
- Adjusting to Zero Trust
- Different from Traditional Corporate model
- Corporate networks restricted, protected, generally assume safe.
- Only managed computers could join, with tight VPN access
- Personal devices frequently restricted or blocked
Zero-Trust grants access based on authentication, not location.
- Different from Traditional Corporate model
2.7.7. Describe defense-in-depth
- Objective: to protect information and prevent unauthorized access
- Layers (in order):
- Physical Security
- Identity & Access
- Perimeter
- Network
- Compute
- Application
- Data
- Physical Security
- Securing access to buildings and computer hardware within data centre
- Intent is to provide physical safeguards against access
- Without physical access, other layers cannot be bypassed
- Lost/Theft handled appropriately
- Identity & Access
- Ensure that identities are secure, necessary, and logged
- Control access to infra and change control
- Use SSO and MFA
- Audit events and changes
- Perimeter
- Protect from network-based attacks
- Use DDoS protection to filter large-scale attacks before users are affected
- Use firewalls to identify and alert malicious attacks against your network
- Network
- Limit communication between resources
- Deny by default
- Restrict inbound access and limit outbound access
- Implement secure connectivity to on-prem networks
- Compute
- Secure access to VMs
- Implement endpoint protection on devices
- Keep systems patched and current
- Application
- Ensure applications are secure and free of vulnerability
- Store sensitive application secrets in a secure storage medium
- Make security a design requirement in application development
- Data
- Attackers are after data that is:
- Stored in a DB
- Store on disk in a VM
- Stored in SaaS applications (O365)
- Managed through cloud storage
- Attackers are after data that is:
2.7.8. Described Microsoft Defender for Cloud
- Monitoring tool for security posture management and threat protection
- monitors cloud, on-prem, hybrid, multicloud environments
- Tools needed to harden resources, protect against cyber attacks, streamline security management
- Natively integrated into Azure
- Protection everywhere you’re deployed
- Many Azure services monitored without any deployment
- In hybrid or multicloud, Azure services are not the complete picture
- Log Analytics agent for this purpose through Azure Arc
- Cloud Security Posture Management (CPSM)
- Azure-Native Protections
- Azure PaaS Services:
- Azure App Service
- Azure SQL
- Azure Storage Account
- etc.
- Azure Data Services
- Networks
- Harden VMs
- Azure PaaS Services:
- Defend your Hybrid Resources
- Add Defender for Cloud using Azure Arc
- Add Defender for Cloud using Azure Arc
- Add Defender for Cloud using Azure Arc
- Defend Resources Running on Other Clouds
- With AWS, you can enable:
- CSPM for AWS CIS, PCI DSS, Foundation Security Best Practices
- Defender for Containers for Amazon EKS Linux
- Defender for Servers for Windows and Linux EC2 Instances
- With AWS, you can enable:
- Assess, Secure, Defend
- Continuously Assess
- Defender for Cloud (VM, Container Registry, SQL Server)
- Defender for Endpoint
- Secure
- Defender for Cloud built on top of Azure Policy controls
- Run on management groups, subscriptions, tenants
- Configures, flags, and recommends
- Supported by Azure Security Benchmark
- Secure score gives you at-a-glance indicator of health of Security Posture
- Defender for Cloud built on top of Azure Policy controls
- Defend
- Security Alerts
- Describe details of affected resources
- Suggest remediation steps
- Provide (in some cases) an option to trigger a response
- All exportable
- Fusion kill-chain Analysis based on cyber kill-chain analysis
- Understand story of attack, where it started, what impact it had
- Continuously Assess
3. Microsoft Azure Fundamentals: Describe Azure Management and Governance
3.1. Describe Cost Management in Azure
3.1.1. Describe Factors that can affect costs in Azure:
- OpEx impacted by:
- Resource Type
- Consumption
- Geography
- Subscription Type
- Azure Marketplace
- Resource Type:
- Type of resource
- Settings of resource
- Region
- Meters track resource usage and generate records
- Consumption:
- Can do Pay-As-You-Go or Reserved Resources
- Reserved Resources provide a discount of up to 72%, but you prepay (1 to 3 years)
- Can still Pay As You go backup, but you have at least X amount of resources
- If you know you have a consistent workload, prepay
- When workload spikes, add with PAYG
- Maintenance:
- Additional resources (i.e Storage/Network) may not deprovision at same time as the main resource (i.e VM)
- Keep an eye on resources to reduce costs
- Geography:
- Global deployment -> global pricing differences
- Resources can differ in cost to deploy on a region basis
- Power, Labor, Taxes, Fees in different regions change
- Network Traffic depends on geography
- Within Europe or US is easier than across continents
- Network Traffic
- Bandwidth: Data moving in and out of Datacenters
- Inbound data Transfer: Data going into datacentres
- Some are free, some are paid
- Outbound data Transfer: Data leaving a datacentre
- Based on zone where you transfer to
- Zone: geographical grouping of Azure regions for billing purposes
- Subscription Type:
- Some subscription types have usage allowances
- Azure free trial allows access to number of products for 12 months
- Also credit is included for 30-days of sign up
- Up to 25 Always-free products (based on resource/region availability)
- Some subscription types have usage allowances
- Azure Marketplace:
- Purchase Azure-based solutions/services from third-party vendors
- i.e server with preinstalled/configured software, firewall, backup services
- You pay for the service as well as the Azure resources
- All Azure Marketplace solutions are certified and compliant with Azure policies and standards
- Purchase Azure-based solutions/services from third-party vendors
3.1.2. Compare the Pricing And Total Cost of Ownership Calculators
- Pricing Calculator:
- Designed to give an estimated cost for provisioning resources in Azure
- Estimate individual resources
- Build out a solution
- Simulate scenarios
- Information purposes only, nothing is actually added to your account when using the pricing calculator
- Designed to give an estimated cost for provisioning resources in Azure
- Total Cost of Ownership (TCO) Calculator:
- Designed to help compare costs for running on-prem compared to cloud infra
- Enter current infrastructure configuration
- Servers
- DBs
- Storage
- Outbound network metrics
- Presented with Cloud configuration offer and difference
3.1.3. Describe the Microsoft Cost Management Tool
- Service to monitor provisioned resources
- What is Cost Management?
- Ability to quickly check resource costs
- Create alerts based on resource spend
- Create budgets to automate management of resources
- Cost analysis: quick visual of Azure costs and forecasts by billing cycle, region, resource, etc.
- Cost Alerts:
- Budget Alerts
- Credit Alerts
- Department Quota Alerts
- Budget Alerts:
- When spending (based on usage or cost) reaches/exceeds amount defined in budget
- Azure Portal = cost
- Azure Consumption API = cost or usage
- Generated automatically, appears in dashboard and emailed to recipient list
- Credit Alerts:
- When credit commitments are consumed
- Used for Enterprise Agreements (EAs)
- Generated Automatically at 90% and 100% of your balance
- Appears in dashboard and emailed to recipient list
- Department Spending Quota Alerts:
- When department spending reaches a fixed threshold of quota
- Configured in EA portal
- Appears in dashboard and emailed to recipient list
- Budgets:
- Where you set a spending limit for Azure
- Based on subscription, resource group, service type, etc.
- Also set a budget alert when you create
- Can also enable budget conditions to automate suspension/modification of resources when trigger occurs.
3.1.4. Describe the Purpose of Tags
- Tags provide metadata about your resources
- Uses:
- Resource management:
- Locate/Act on resources associated with specific workloads, environments, business units, and owners.
- Cost management & Optimization:
- Group resources to report on costs, track budgets, etc.
- Operations Management:
- Group resources based on business critical criteria, and availability
- Helps formulate Service-Level Agreements (SLA: uptime/performance guarantee between you and users)
- Security:
- Classify by public/confidential security
- Governance/Regulatory Compliance:
- Identify resources that align with compliance requirements (ISO 27001)
- Can also be tagged with owner/department name
- Workload Optimization and Automation:
- Tags help visualize all resources that participate in complex deployments
- Tag with application name and use Azure Devops to automate
- Resource management:
- How do I manage resource tags?
- PowerShell, Azure CLI, Azure Resource Manager templates, Azure REST API, Azure Portal.
- Azure Policy can enforce tagging rules and conventions
- Require tags be added to new resources on provision
- Define rules that reapply removed tags
- Resources don’t inherit tags from subscriptions and resource groups
3.2. Describe Features and Tools in Azure for Governance and compliance
3.2.1. Describe the purpose of Microsoft Purview
- Family of data governance, risk, compliance solutions
- Insight about on-prem, multicloud, SaaS data
- Provides Automated data discovery, sensitive data classification, E2E data lineage
- Risk and Compliance Solutions
- Microsoft 365 Teams, OneDrive, Exchange use Purview
- Helps orgs protect sensitive data, identify risks, and manage regulatory compliance requirements
- Unified Data Governance:
- Create an up-to-date map of your entire data estate that includes data classification and end-to-end lineage.
- Identify where sensitive data is stored in your estate.
- Create a secure environment for data consumers to find valuable data.
- Generate insights about how your data is stored and used.
- Manage access to the data in your estate securely and at scale.
3.2.2. Describe the purpose of Azure Policy
- Service that enables you to create, assign, manage policies that control and audit resources
- Enforce rules across resource configurations to be compliant with corporate standards
- How does Azure Policy define policies?
- Define individual policies and groups of policies (initiatives)
- Evaluates resources and highlights non-compliant resources
- Can also prevent non-compliant resources from being created
- Can set policies at resource/group/subscription/etc. levels
- Policies are inherited (parent-child)
- Built-in Policy and Initiative definitions for Storage/Networking/Compute/Security Center/ Monitoring.
- Can also automatically remediate non-compliant resources and configurations
- Integrates with Azure DevOps for CI/CD pipelines
- What are Azure Policy Initiatives?
- Way of grouping related policies together
- i.e “Enable Monitoring” in Azure Security Center includes the following and more:
- “Monitor unencrypted SQL Database in Security Center”
- “Monitor OS vulnerabilities in Security Center”
- “Monitor missing Endpoint Protection in Security Center”
3.2.3. Describe the purpose of Resource Locks
- Prevents resources from being accidentally deleted or changed
3.2.4. Describe the purpose of the Service Trust Portal
- Portal that provides access to content, tools, and other resources about Microsoft security/privacy/compliance practices.
- Details about Microsoft’s implementation of controls and processes that protect services and customer data
- There is an NDA to accept for compliance materials
3.3. Describe Features and Tools for Managing and Deploying Azure resources
3.3.1. Describe Tools for Interacting with Azure
- What is the Azure Portal?
- web-based console, manage by GUI
- Build, Manage, Monitor all deployments
- Create custom dashboards
- Configure accessibility options
- Present in every Azure datacenter, and is deployed on “edge”
- Azure Cloud Shell
- browser-based shell tool
- Supports Azure PowerShell and Azure CLI (bash)
- Authenticated to Azure credentials
- Azure PowerShell
- Interface to Azure REST API
- Scripting language (PowerShell)
- Azure CLI
- Interface to Azure REST API
- Scripting language (Bash)
3.3.2. Describe Purpose of Azure Arc
- Arc extends compliance/monitoring to hybrid and multicloud configuration
- Centralized way to:
- Manage all environments together by projecting non-Azure resource into ARM
- Manage multi-cloud, hybrid VMs, Kubernetes Clusters, DBs in Azure
- Use familiar services and management capabilities on all resources
- Continue using traditional ITOps while introducing DevOps practices
- Configure custom locations as abstraction layers on top of clusters.
3.3.3. Describe Azure Resource Manager (ARM), templates, and Bicep
- Deployment/management Service for Azure
- Layer to CRUD resources in Azure Account
- Includes the Azure REST API
- Benefits:
- manage infra through JSON templates
- deploy/manage/monitor resources in groups
- Re-deploy through the Software Development Life Cycle (SDLC) consistently
- Define dependencies between resources, and deploy in correct order
- Apply RBAC to all services
- Apply tags to resources
- View billing
- Infrastructure as Code (IaC)
- Manage infra as code
- Benefits of ARM Templates:
- Declarative Syntax
- Repeatable Results
- Orchestration
- Modular Files
- Extensibility with PWSH or Bash
- Bicep
- Language to deploy Azure resources
- Defines Infrastructure and Configuration
- Bicep is simpler, more concise than ARM Templates
- Immediately supports preview and versions of Azure services
- All the benefits of ARM Templates minus PWSH and Bash
3.4. Describe Monitoring Tools in Azure
3.4.1. Describe Purpose of Azure Advisor
- Evaluates Azure resources and makes recommendations
- Designed to save time on cloud optimization
- Take actions, postpone, or dismiss
- Available to provide notifications and alerts for new recommendations
- Dashboard displays personalized recommendations for all subscriptions
- Can be filtered
- Categories: Reliability, Security, Performance, Operational Excellence, Cost.
3.4.2. Describe Azure Service Health
- Azure Status is global Azure status and outages
- Service Health focuses on your Azure regions and services
- Resource Health is a view of your Azure resources
- Together, all provide complete view of your Azure environment from global to specific resources.
3.4.3. Describe Azure Monitor
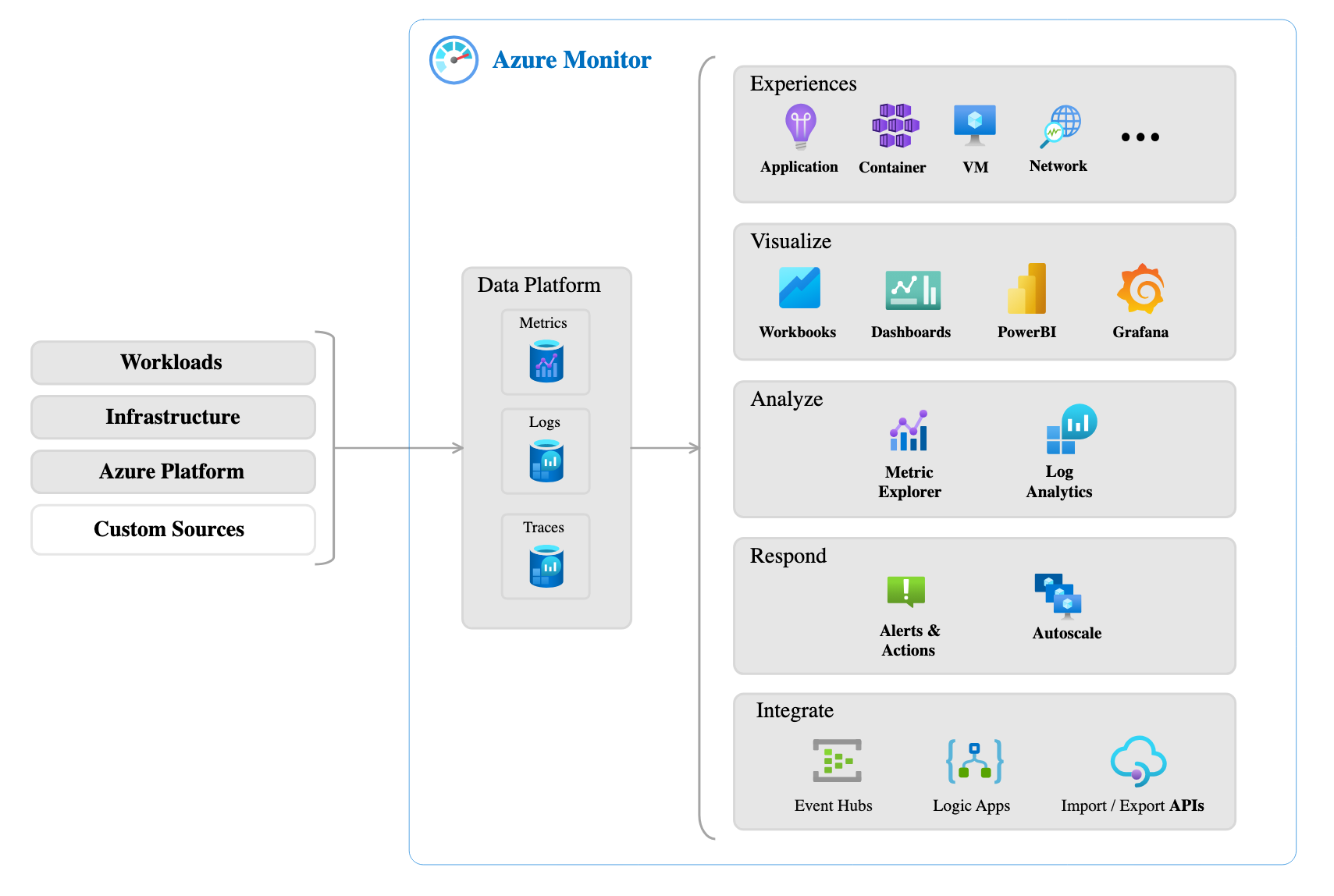
- Platform for collecting, analyzing, visualizing, and acting on data based on your resources.
- Can monitor Azure, on-prem, and multi-cloud resources.
- Use data to help react to events in real-time via SMS, Email, Autoscaling resources, etc.
- Azure Log Analytics
- Write/Run log queries on data gathered by Azure Monitor
- Can sort/filter/analyze records
- Advanced queries for statisticaly analysis and visualization of trends
- Azure Monitor Alerts
- Automated way to stay informed when thresholds are crossed in Azure Monitor.
- Provides the notification service, and can attempt corrective action on resources.
- Can monitor logs and metrics and trigger events.
- Application Insights
- Monitor web apps in Azure, on-prem and multicloud
- SDK in application or agent on your VM
- Metrics Monitored:
- Request rates, response times, failure rates
- Dependency rates, response times, failure rates (external services)
- Page views, browser performance
- AJAX calls from pages (rates, response times, failure)
- User/Session Counts
- CPU/memory/network usage